Traffic Management in Kubernetes with two Ingress Controllers
A popular scenario I see with my clients is this:
Several microservices need to communicate internally using specific private domains and paths, such as:
- kuberise.internal/service-a
- kuberise.internal/service-b
At the same time, some microservices must be accessible externally with valid DNS domains, like:
- kuberise.io/front-end
The challenge? Ensuring no external traffic can access internal microservices while efficiently routing traffic both internally and externally.
In cases like this, Kuberise.io provides a solution by leveraging two instances of the Nginx Ingress Controller:
👉 Internal Ingress Controller: Handles traffic between internal microservices using kuberise.internal or your chosen internal domain.
👉 External Ingress Controller: Manages traffic from external clients to exposed services, using DNS configurations and TLS as needed.
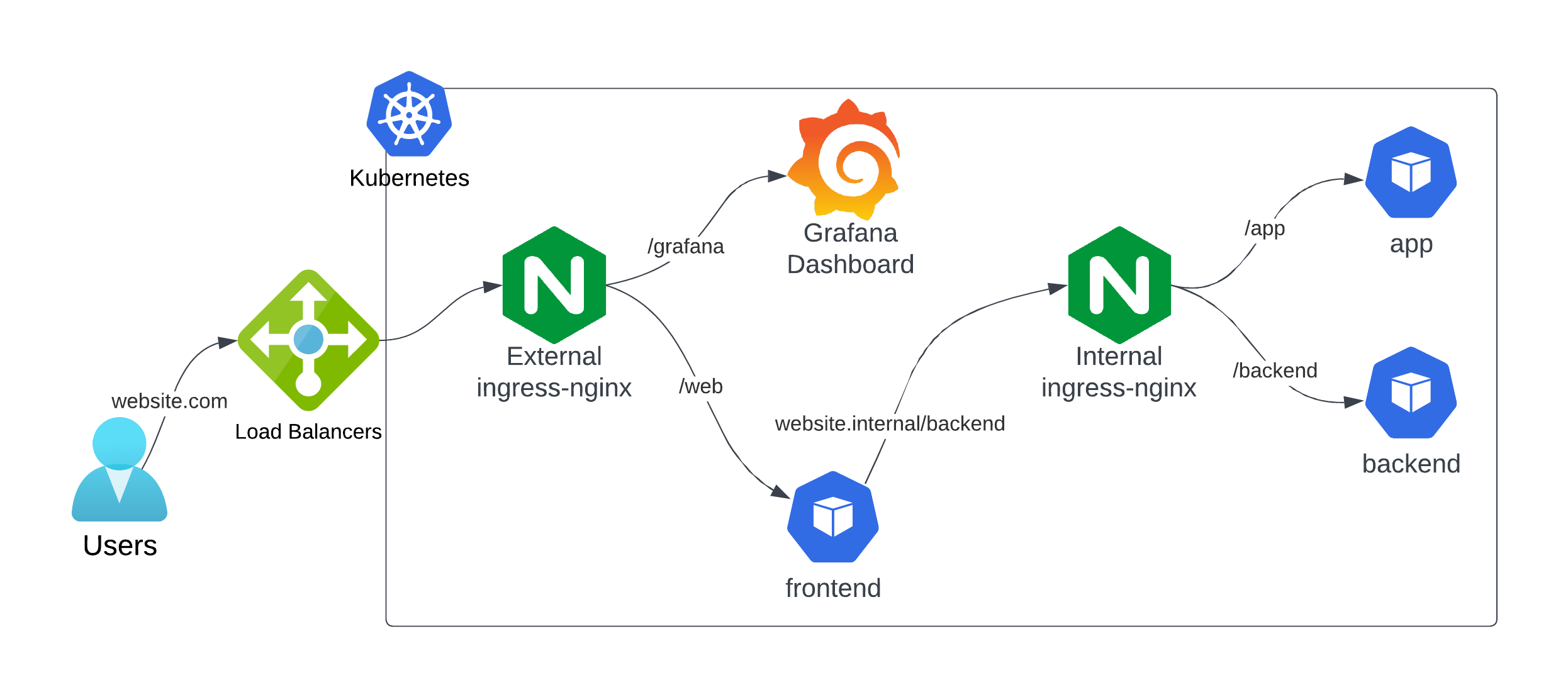
As part of Kuberise.io’s reference architecture, this setup allows for:
✅ Clear separation of internal and external traffic.
✅ Secure and optimized routing with customizable domains like kuberise.internal and ingress classes.
✅ Built on the GitOps model with platform engineering best practices and platform consistency.
🔗 Want to learn more? Explore how to configure Nginx Ingress Controllers and generic deployment helm chart with Kuberise.io here: https://kuberise.io/docs/platform-tools/nginx-ingress-controller
