HTTPS to Backend
By default, requests to services will go to the ingress-nginx service first. Ingress-nginx will terminate the SSL and send HTTP traffic to the backend service.
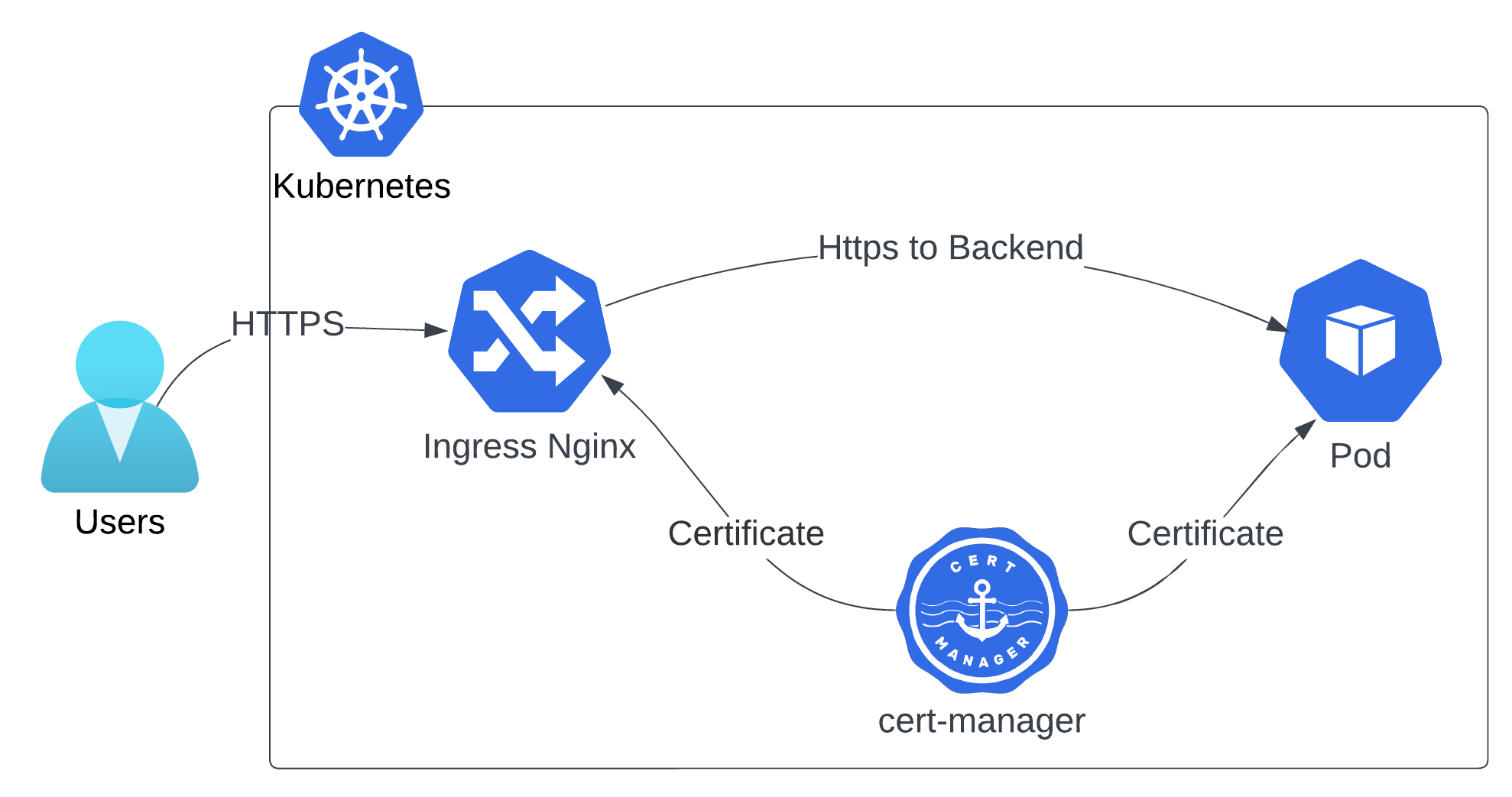
While some consider this architecture secure enough, others prefer to secure the communication between ingress-nginx and pods as well. In this tutorial, you will learn how to do it.
We will use the same certificate that is generated for this service for ingress controller by cert-manager. But we will ask from cert-manager to generate it again in a kubernetes secret in the namespace of the service. Then we will mount it to the pod to be used by the application inside the pod, and we will ask ingress-nginx to send the traffic to the pod using HTTPS.
Assumptions
- You have deployed Kuberise.io in your Kubernetes cluster.
- You have already added your tool and service into your Kuberise.io platform, and it has an HTTPS certificate and ingress. However, the backend traffic from ingress-nginx to the pod is HTTP and not encrypted.
- You are using the generic-deployment template for your service.
Steps to Secure Backend Communication
1. Enable HTTPS for Backend Service
To enable HTTPS for the backend service, you need to modify the values.yaml file of your service to set useHttps to true.
useHttps: true
2. Configure Ingress Annotations
Ensure that the ingress annotations in your values.yaml file specify that the backend protocol is HTTPS. Also add the annotation for the cert-manager cluster issuer and add a secretName for a kubernetes secret to store the certificate. In the host section, use the service name and the domain name. {{ $.Values.domain }} is the domain name of the cluster that you defined in the Kuberise.io installation and {{ include "generic-deployment.fullname" . }} is the service name. You can change the service name if you want.
ingress:
annotations:
nginx.ingress.kubernetes.io/backend-protocol: "HTTPS"
cert-manager.io/cluster-issuer: "selfsigned-clusterissuer"
tls:
- secretName: "backend-https-tls"
hosts:
- '{{ include "generic-deployment.fullname" . }}.{{ $.Values.domain }}'
3. Define Service Ports
Update the service ports to include HTTPS.
service:
type: ClusterIP
ports:
https: 443
4. Configure Deployment
Ensure that the deployment configuration uses the correct container port for https protocol and volume for the certificate in the kubernetes secret.
containerPorts:
https: 8443
volumes:
- name: tls-cert
secret:
secretName: backend-https-tls
volumeMounts:
- name: tls-cert
mountPath: /etc/nginx/certs
readOnly: true
5. Apply Probes
Update the liveness, readiness, and startup probes to use HTTPS if necessary.
livenessProbe:
httpGet:
path: /
port: https
scheme: HTTPS
initialDelaySeconds: 10
periodSeconds: 10
timeoutSeconds: 1
failureThreshold: 3
readinessProbe:
httpGet:
path: /
port: https
scheme: HTTPS
initialDelaySeconds: 5
periodSeconds: 5
timeoutSeconds: 1
successThreshold: 1
failureThreshold: 3
startupProbe:
httpGet:
path: /
port: https
scheme: HTTPS
initialDelaySeconds: 0
periodSeconds: 10
timeoutSeconds: 1
failureThreshold: 30
By following these steps, you can secure the communication between ingress-nginx and your backend pods, ensuring that all traffic within the cluster is encrypted.
